ADRA NDR to aplikacja cyberzabezpieczeń działająca na dedykowanych modelach sprzętu QNAP w celu chronienia wewnętrznej sieci urządzeń przed ukierunkowanymi atakami złośliwego oprogramowania.
Respond to threats by your selected rule
Once malware activities are detected, configured response actions will be taken based on the selected rule.
Defend threats with user-friendly GUI
The ADRA NDR software provides an overview dashboard and a user-friendly GUI to help IT staff efficiently detect and analyze network threats.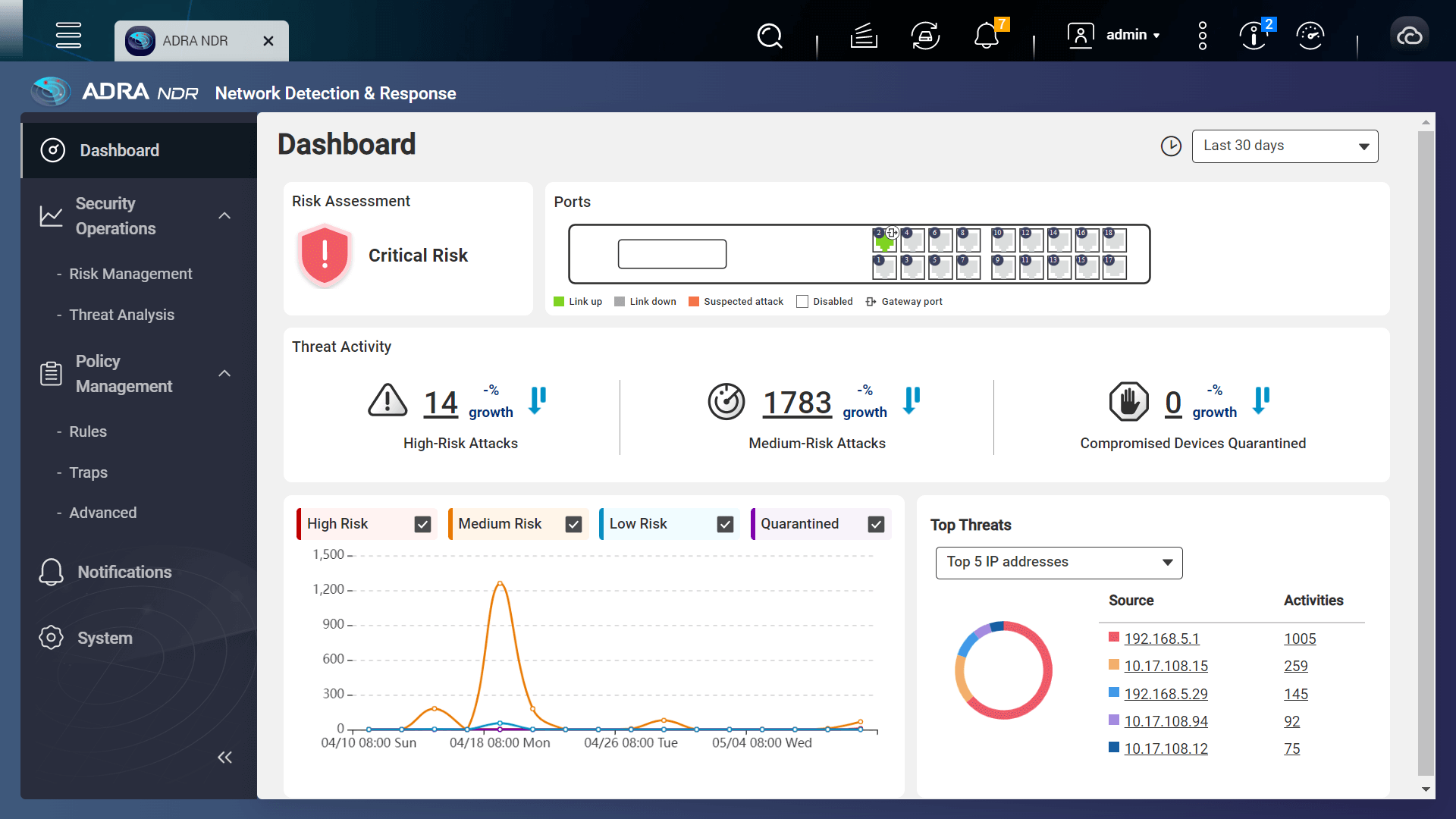
Implement ADRA NDR solution in your factories and offices
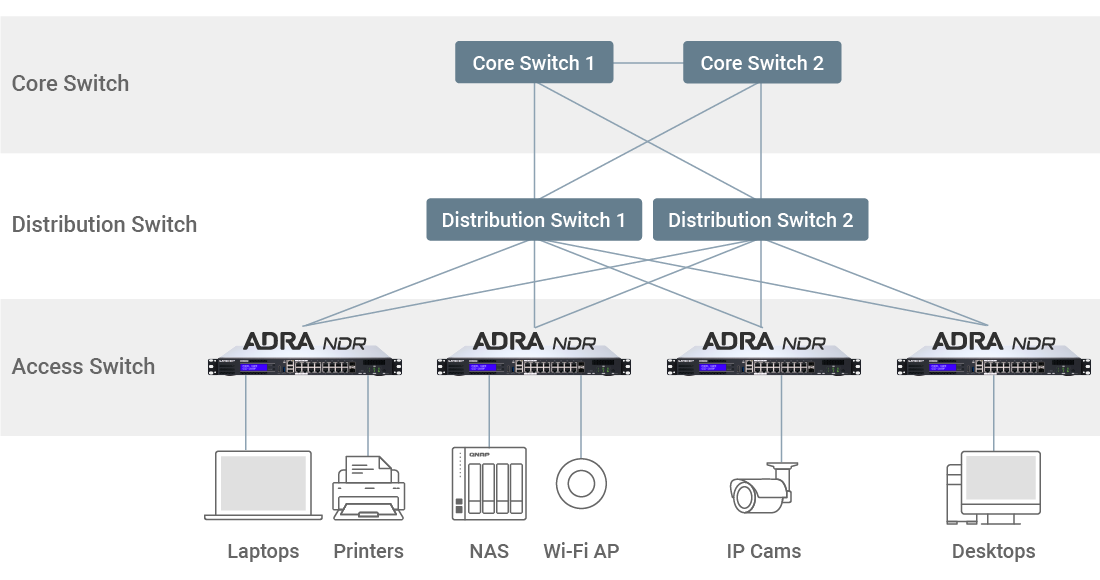
The QGD-1602P ADRA NDR appliance is designed to replace existing access switches that are directly connected to end devices such as computers, printers, IP cameras, and other connected devices. This deployment method can effectively maximize your defense coverage by the cybersecurity appliance. Once connected, the QGD-1602P will scan for anomalies to-and-from end devices and react to detections.
Layer 2 management and PoE
The QGD-1602P comes with comprehensive Layer 2 management features to help IT staff efficiently manage entire networks. These features include virtual LAN, link aggregation (port trunking), quality of service (QoS), and more. Furthermore, the QGD-1602P is equipped with power over ethernet (PoE) to further expand the flexibility of the cybersecurity appliance. An intuitive user interface is available to view switch status including PoE power supplies information and to configure network settings.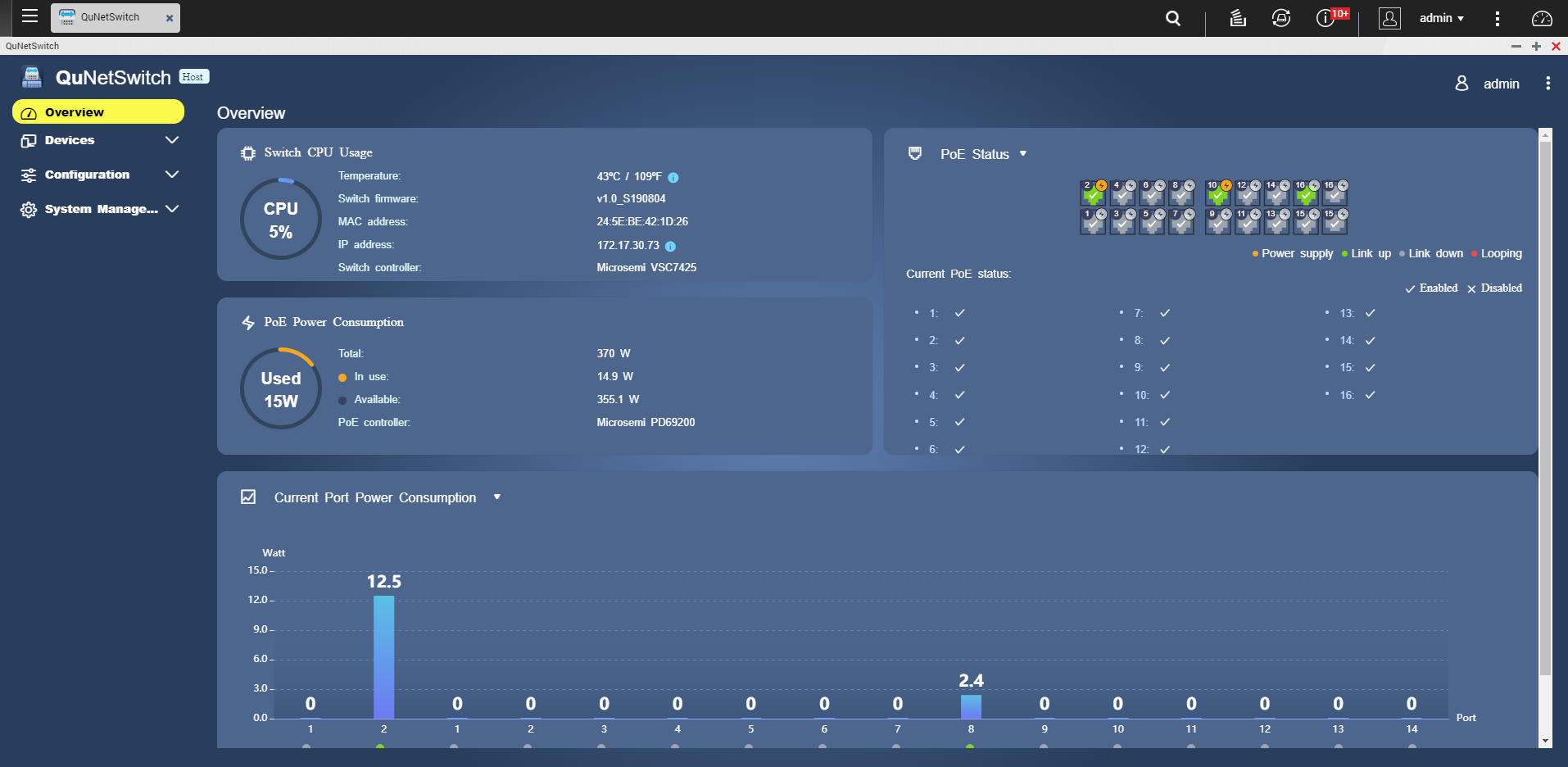
Pair with any NAS to safeguard digital assets
NAS is often entrusted with valuable personal and business data and this makes it a frequent target of malware such as targeted ransomware. The QGD-1602P can protect storage environments with NAS devices of all brands, assisting in scanning traffic to NAS devices for hostile actions and effectively protecting private and confidential data from malicious activities.
Stay ahead of systemwide cyber criminals
Deploy the QGD-1602P cybersecurity appliance for devices with strategic importance, such as NAS. To achieve maximum coverage against most threat types, it is recommended to install multiple QGD-1602P for all devices at the access switch level for fast-screening of malware such as targeted ransomware. The 10GbE ports of the QGD-1602P serve as fast lanes to aggregation switches or NAS, boosting performance for your network topology.